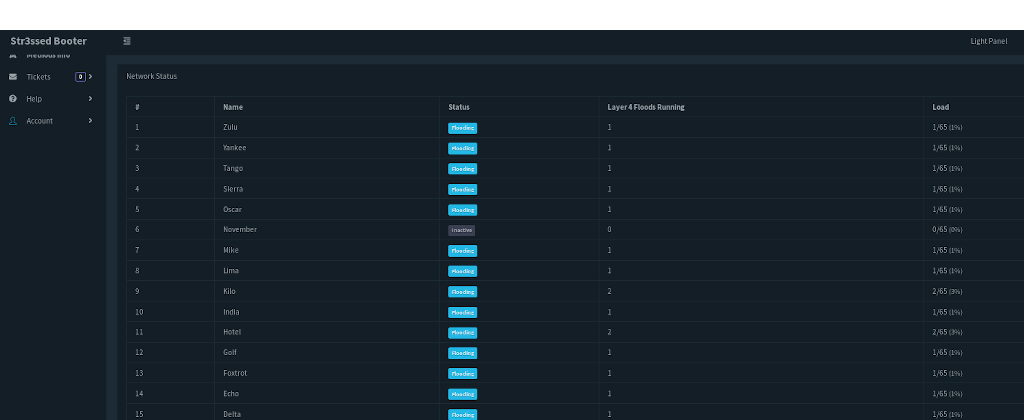
Booter is actually a program which can be used to break into and incident other people’s computer systems. It produces thousands of packages for the sufferer, that may eventually overcome their program and cause it to accident. This distribute discusses how this strike performs, what makes up prohibited booters, and possible defences against this sort of happens.
It’s typically the most popular software on the internet, ask for anyone. Why do individuals use booters? It might be for a number of elements, but it really all boils down to one important thing: they’re extremely lazy and don’t need to work tirelessly. That’s proper should you be such as every single day life is too easy or that this circumstance is moving too effectively, you will desire a fantastic outdated-designed volume of negativity in your life with this particular fantastic system.
What is a booter application?
A stresser application is the word for just about any program that can be used to transform off other personal computer solutions. This is made up of programs like shutdown, reboot, and possible away from. Online hackers or pranksters often make use of them to result in damage on a person else’s computer team. Even though they may have some legit use circumstances, these plans are typically frowned upon primarily because it needs time for that target to get their method back once more.
What could it do?
Booter application is a kind of personal computer software program which is designed to relieve denial-of-assistance assaults. It can be used by anybody mindful of how it operates without having any specialised understanding or capabilities. These plans are quick and simple for newbie shoppers. The attacker can strike off an assault in a personal computer in one more region with only a couple clicks of the computer mouse move. This kind of plans provide the consumer due to the information concerning their targets like Ip, hostname, slot assortment and in some cases username if accepted upfront.
A benefit of employing these strategies is that they will not call for constant oversight, contrary to other hacking tools like proxy hosts or VPNs, that you just must constantly keep close track of to preserve better-effectiveness degrees.